Data breaches are like the unexpected guests who crash your party, eat all the snacks, and leave your secrets scattered across the Internet. One moment you're peacefully browsing cat videos, and the next, your email is plastered across dubious websites, promising riches if only you click a suspicious link. It's a modern-day nightmare that can affect everyone from individuals to large corporations. The digital age has brought convenience, but it also comes with its own set of perils that we must navigate cautiously.
In today's interconnected world, data breaches have become alarmingly common, with headlines frequently announcing the latest victims. Whether it's a social media giant or a small business, no one is immune to the threat. This article delves into the fascinating and sometimes humorous world of data breaches, from the masterminds behind them to the far-reaching consequences they create.
The Notorious Hackers
Let's face it—hackers are the rock stars of the cyber world. With pseudonyms like "ShadowPhantom" and "ByteBuster," they could easily headline a concert tour. Instead, they headline news articles, causing more drama than a celebrity feud. Their tools of the trade? A mix of clever coding, social engineering, and occasionally, plain old luck. These digital daredevils often operate in the shadows, their identities concealed by layers of anonymity. Some are motivated by money, others by ideology, but all share a knack for finding and exploiting vulnerabilities in our digital lives.
Hackers come in various forms and with differing motivations. There are "black hat" hackers, who engage in malicious activities for profit, political reasons, or simply for the thrill. On the opposite end, "white hat" hackers use their skills to improve security by identifying vulnerabilities and helping fix them. Then there are "gray hat" hackers, who fall somewhere in between, sometimes violating laws to expose security flaws but without malicious intent. Understanding these different types of hackers is crucial in grasping the full spectrum of cyber threats.
The Sneaky Techniques
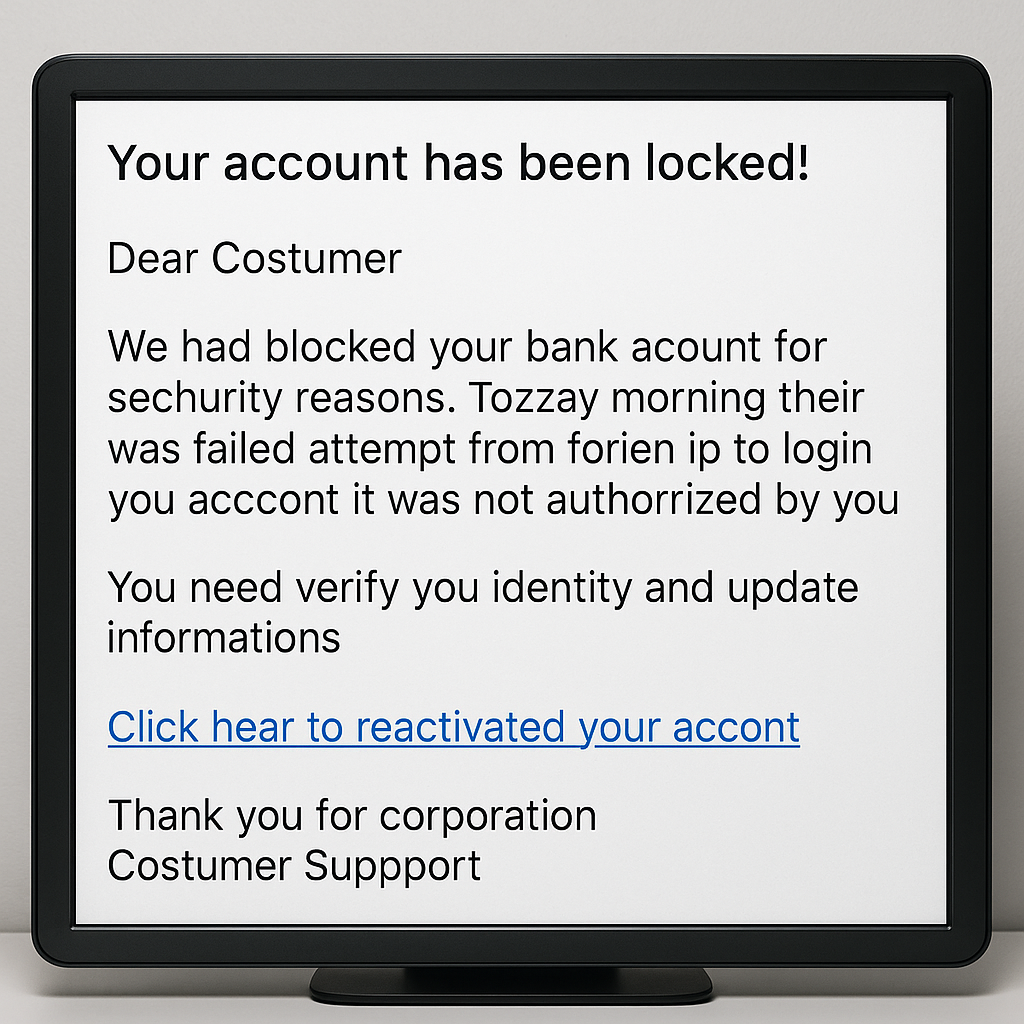
Hackers have their ways—phishing emails that are more convincing than your best friend's messages, malware that hides in the nooks and crannies of your system, and ransomware that holds your files hostage like a villain in an action movie. Just remember, clicking on that "Congratulations! You've won a million dollars!" link is never a good idea. Phishing scams can be incredibly sophisticated, mimicking legitimate sites and communications to trick even the most cautious among us. Malware is another favorite tool, silently infiltrating systems and wreaking havoc. And then there's ransomware, which forces victims into a harrowing dilemma: pay the ransom or lose access to crucial data.
Phishing, one of the most common techniques, involves tricking individuals into revealing personal information through deceptive emails or websites. These messages often appear genuine, coming from trusted sources like banks or colleagues, and can lead to significant breaches once the information is obtained. Malware, on the other hand, includes viruses, spyware, and Trojans designed to infiltrate and damage systems. Finally, ransomware attacks have become increasingly prevalent, with hackers encrypting data and demanding payment for its release, often leaving victims with a sense of helplessness.
Headlines That Capture Attention
When a data breach hits, it's akin to a blockbuster movie release. News outlets scramble to report the juiciest details—how many accounts were compromised, the mysterious hacker group behind it, and the extent of the chaos. It's the kind of drama that keeps people glued to their screens, popcorn in hand. Each breach comes with its own narrative, often involving high-stakes intrigue and the race to contain the fallout. The public follows these stories with morbid fascination, waiting to see how the affected parties will respond and what measures they'll take to prevent future breaches.
The media plays a significant role in shaping public perception of data breaches. Sensational headlines draw attention, creating a sense of urgency and concern among readers. Details such as the number of affected users, the type of data compromised, and the potential consequences are dissected and analyzed. This coverage not only informs the public but also pressures companies to respond swiftly and transparently, often leading to improvements in security measures and protocols.
The Ripple Effect
Data breaches don't just affect the hacked company; they ripple through the entire digital ecosystem. From stock market dips to sudden spikes in cybersecurity budgets, the impacts are felt far and wide. It's a bit like a soap opera where everyone gets pulled into the drama. Companies may face lawsuits, regulatory fines, and a loss of consumer trust, which can take years to rebuild. The broader economy can also be affected, as businesses reevaluate their security practices and invest in stronger defenses. Meanwhile, consumers become more vigilant, often changing their habits to protect their personal information.
The aftermath of a data breach can be extensive and multifaceted. Companies involved in breaches often see an immediate impact on their stock prices as investors react to the news. Legal repercussions can follow, with affected individuals or entities seeking compensation through lawsuits. Additionally, regulatory bodies may impose fines and penalties, further straining the company's resources. On a broader scale, industries may tighten their security standards, prompting a surge in demand for cybersecurity professionals and technologies. For consumers, the breach serves as a wake-up call to better protect their digital footprint.
The Personal Fallout
For the average person, a data breach is the digital equivalent of losing your wallet in a crowded market. Suddenly, you're checking bank statements with the intensity of a detective on a TV crime show. Passwords get changed faster than fashion trends, and you develop a newfound paranoia towards your inbox. Identity theft is a real concern, with thieves potentially using your information to commit fraud or other crimes. The stress and uncertainty can be overwhelming, driving home the importance of proactive measures like robust passwords and two-factor authentication.
The personal consequences of a data breach can be deeply unsettling. Victims may experience financial loss, damage to their credit score, and a prolonged period of uncertainty as they work to secure their accounts. The emotional toll can be significant, leading to stress, anxiety, and a sense of vulnerability. In response, many individuals adopt stricter security practices, such as regularly updating passwords, enabling two-factor authentication, and monitoring accounts for suspicious activity. These steps, while time-consuming, can provide a greater sense of control and security in the digital world.
The Humorous Side
But amidst the chaos, there's always room for humor. Like the time someone tweeted, "Just got hacked; hackers, please add some money to my account!" Or the countless memes depicting hackers as dark, hooded figures typing furiously in dimly-lit rooms. The Internet, as always, finds a way to laugh through the madness. Humor can be a coping mechanism, helping people deal with the anxiety and frustration that come with data breaches. It also highlights the absurdity of the situation, reminding us that even in the darkest times, there's a silver lining to be found.
Humor can serve as an important coping mechanism, helping individuals and communities process the stress and frustration that accompany data breaches. Social media platforms are often abuzz with witty comments, jokes, and memes that poke fun at the situation. This collective laughter not only lightens the mood but also fosters a sense of solidarity among those affected. By finding humor in the absurdity of data breaches, we can alleviate some of the tension and remind ourselves that we're all in this digital landscape together, navigating its ups and downs.
Conclusion
Data breaches are no laughing matter, but understanding their impact—from the notorious hackers to the sensational headlines—can help us navigate the digital landscape with a bit more awareness and a touch of humor. So, next time you're online, remember to stay vigilant, keep your passwords secure, and maybe laugh a little at the absurdities of the cyber world. While it's important to take cybersecurity seriously, maintaining a sense of humor can make the journey a bit more bearable. After all, we're all in this digital adventure together.
In conclusion, data breaches highlight the vulnerabilities inherent in our digital lives. By staying informed and adopting best practices for online security, we can mitigate the risks and protect our personal information. And amidst the challenges, it's vital to keep a sense of humor and perspective, recognizing that while data breaches are a serious issue, they also present an opportunity for growth, learning, and community resilience.