- Angie MarCo
- June 5, 2025
- Cybersecurity and Protection
The Wi-Fi Is Lava: Why You Should NEVER Connect to Public Networks
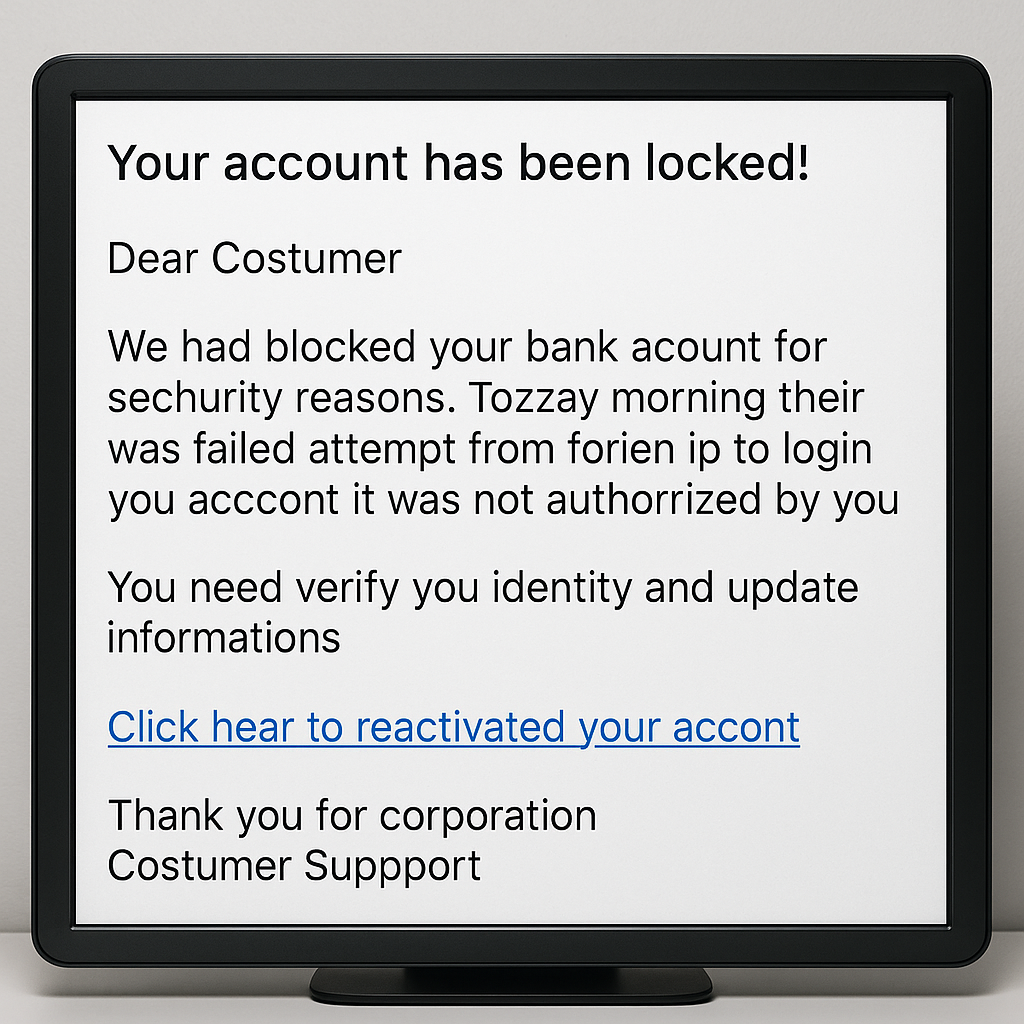
If your childhood was anything like mine, you’ve played the game “The Floor Is Lava.” You’d leap from couch to chair, avoiding imaginary molten death, because who wants their legs roasted like marshmallows? Fast forward to adulthood, and I’m here to tell you there's a modern remake of this game—but it’s not imaginary. It’s called “The Wi-Fi Is Lava,” and playing it might just save your digital life.
Read More